We’ve found quite a few things that weren’t disclosed by them during the sale and the inspector didn’t catch.Those are long existing defects. We’re they disclosed to you as part of the sale? If not, I’d contact your real estate agent or a lawyer.
Home Theater
Entertainment & Streaming Content
Physical Media
Home Theater Equipment and Hardware
Other Diversions
Bargains and Classifieds
Home Theater Forum
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
What annoys you? (1 Viewer)
- Thread starter Alf S
- Start date
More options
Who Replied?Chip_HT
Screenwriter
- Joined
- Jun 28, 2004
- Messages
- 1,096
- Real Name
- Chip
As life goes on, these passwords are getting more and more complicated, and you are supposed to use a different one for each site. How many “ZUTV4$&s” can you memorize?
What gets funny is what websites/services require what level of password intensity.
At work, our scheduling software requires all four of uppercase, lowercase, numbers, and symbols (but at least it doesn't expire). That's more intense than our e-mail password, which only requires three of those but expires every three months.
But then the e-mail password system gets stupid. Individuals can reset their password a number of ways by themselves online, and can form any password they want. But if an e-mail account is a shared account, there is one specific person who has to call in every 90 days and get a "randomly generated" set of characters, so you can never get anything that's easy to remember. Seems a little backwards to me. If the account is shared, it seems like it would be a less secure account anyway.
Although I'm wondering how random those passwords are. During one of the password resets last year, the IT guy didn't want to be bothered by this ordeal and I could tell we pissed him off when he read the password out, starting with a tilde, a couple of letters and numbers, another symbol, more letters, and ended with a vertical line. But then the next time we called, we got the letters from the final round of Wheel of Fortune as the password. Somehow the last two resets have given us actual words.
I get annoyed that organizations resort to these old, outdated, and insecure password methods, completely ignoring the current NIST "Best Practices" standard. As someone who regularly deals with passwords and resets I can say with authority, people *will* write down passwords, especially "complex" ones, and leave them in obvious places:
NIST Password Standards
The best practices outlined in the NIST SP 800-63 are the latest NIST password guidelines to enter the industry. Previously modified in 2017, today’s NIST password standards flip the script on many of the organization’s historic password recommendations—earning applause from IT professionals across the country. Here are some of the most important changes for MSPs:- The more the merrier: The new NIST password guidelines suggest an eight-character minimum when the password is set by a human, and a six-character minimum when it’s set by an automated system or service. They also recommend encouraging users to create lengthy passwords with a maximum length of 64 characters or higher. All applications must permit any printable characters listed within the American Standard Code for Information Interchange, including spaces, and should even accept UNICODE characters (like emojis).
- Remove the reset: For years, most MSPs have encouraged their customers to put password reset policies in place, requiring employees to change their passwords every few months or so. According to NIST, this should no longer be the case. The organization explains the reset periods have proven more detrimental than constructive. As users struggle to drum up countless creative, strong new passwords each month, they end up creating weaker passwords. Password strength should be about quality, not quantity—one excellent password is better than 10 new, mediocre ones.
- Complexity isn’t king: How often have you created a new account, for a new application, online store, or digital news outlet, and encountered the prompt, “your password must contain one lowercase letter, one uppercase letter, one number, and one symbol”? For years, this type of configuration was the norm. But NIST now explains—much like the new reset recommendation—overly complex passwords can lead to poor password behavior. Users who forget their complicated passwords tend to end up replacing them with new, weaker ones.
- Make it a user-friendly affair: The “show password while typing” is a rare option on many login sites. NIST suggests changing this, allowing more users to view their passwords as they enter them. Without this option, users are more inclined to choose shorter passwords that are easier to enter correctly. Shorter passwords are less secure, so any benefits gained from these visibility blocks are counteracted by weaker passwords.
- Lose the clues: Some accounts will allow users to access a personal hint or provide an answer to a pre-selected question, like “what was the name of your first pet?” when they forget their credentials. But while knowledge-based authentication clues can save users from the hassle of creating a new password, they are also risky. Personal data abounds in today’s digital era, making it easier than ever for hackers to decode hint prompts and breach systems. So while these clues may save time, foregoing these options is in everyone’s best interest.
- Limit the attempts: Enabling an unlimited number of password attempts may temporarily help users who have forgotten their passwords, but they end up doing more harm than good. The latest NIST password standards recommend providing users with a maximum of 10 login attempts before they are turned away—enough to aid a forgetful user, but not enough to assist brute-force attackers.
- A hands-free approach: Driving laws aren’t the only regulations cracking down on texting. The NIST two-factor authentication (2FA) policy states that, while 2FA is still important, SMS texting services should not be a part of the process. SMS delivery isn’t entirely secure, providing advanced cybercriminals with an opportunity to insert malware into the system. This malware can redirect text messages and facilitate attacks against the mobile phone network—which is why SMS texting should be avoided entirely.
Jeffrey D
Senior HTF Member
- Joined
- Oct 15, 2018
- Messages
- 5,221
- Real Name
- Jeffrey D Hanawalt
My method of combating the requests for password changes is I have 3 or 4 variations of the same word/number code, and I change them when prompted so I don’t forget what the password is.
I have, and recommend, 3 or 4 passwords built from phrases and using the first letter of each word with numbers added. You then increment the number when a change is mandated.
example:
the phrase:
my father's name is fred and my brother's name is bob
becomes
mfnifambnib
then add a 2 digit number (front and/or back)
mfnifambnib01
At the next password change, increment the number. All you have to truly remember is the current number.
Should a "special" character be required, put it on one end. If capitalization is required, capitalize the proper noun letters or pick a word at random to capitalize.
example:
the phrase:
my father's name is fred and my brother's name is bob
becomes
mfnifambnib
then add a 2 digit number (front and/or back)
mfnifambnib01
At the next password change, increment the number. All you have to truly remember is the current number.
Should a "special" character be required, put it on one end. If capitalization is required, capitalize the proper noun letters or pick a word at random to capitalize.
jcroy
Senior HTF Member
- Joined
- Nov 28, 2011
- Messages
- 7,932
- Real Name
- jr
For passwords, it is highly dependent on the website.
For a high security website, I'll use a completely different password which common cracking programs take a long time to crack by a dictionary attack.
The trick is finding something which can't be cracked easily by common password cracking programs. This means it is not an immediate dictionary word, nor any obvious widely known substitutions (such as leet speak) inserted into a common dictionary word.

 en.wikipedia.org
en.wikipedia.org
There's various text files of leaked (or cracked) passwords which will give a good idea what a cracking program will use as a starting point.
For a high security website, I'll use a completely different password which common cracking programs take a long time to crack by a dictionary attack.
The trick is finding something which can't be cracked easily by common password cracking programs. This means it is not an immediate dictionary word, nor any obvious widely known substitutions (such as leet speak) inserted into a common dictionary word.

Leet - Wikipedia
There's various text files of leaked (or cracked) passwords which will give a good idea what a cracking program will use as a starting point.
jcroy
Senior HTF Member
- Joined
- Nov 28, 2011
- Messages
- 7,932
- Real Name
- jr
I have, and recommend, 3 or 4 passwords built from phrases and using the first letter of each word with numbers added. You then increment the number when a change is mandated.
example:
the phrase:
my father's name is fred and my brother's name is bob
becomes
mfnifambnib
then add a 2 digit number (front and/or back)
mfnifambnib01
This is the sort of algorithm which has been recommended by a few hardcore hacker types.
As far as I can figure out, the common password cracking programs have only really started looking into algorithms of this type. For example, such as taking huge lists of common phrases and generating password strings from the first letter of each word in a phrase.
My guest wifi password is:
ywngtwp###
where ### is my house number. The phrase is "you will never guess the wifi password" - and my son just doesn't *get* that "password" is *one* word, not two. Every time he comes in with a new device he messes it up and I have to remind him password is *one* word.
ywngtwp###
where ### is my house number. The phrase is "you will never guess the wifi password" - and my son just doesn't *get* that "password" is *one* word, not two. Every time he comes in with a new device he messes it up and I have to remind him password is *one* word.

TJPC
Senior HTF Member
We use variations including the name of a much beloved long dead pet. We also have no social media presence which might include details of our personal lives for clues.
jcroy
Senior HTF Member
- Joined
- Nov 28, 2011
- Messages
- 7,932
- Real Name
- jr
There's various text files of leaked (or cracked) passwords which will give a good idea what a cracking program will use as a starting point.
For example, a public list of the 10,000 most common password listed on wikipedia.
Wikipedia:10,000 most common passwords - Wikipedia
jcroy
Senior HTF Member
- Joined
- Nov 28, 2011
- Messages
- 7,932
- Real Name
- jr
Complexity isn’t king: How often have you created a new account, for a new application, online store, or digital news outlet, and encountered the prompt, “your password must contain one lowercase letter, one uppercase letter, one number, and one symbol”? For years, this type of configuration was the norm. But NIST now explains—much like the new reset recommendation—overly complex passwords can lead to poor password behavior. Users who forget their complicated passwords tend to end up replacing them with new, weaker ones.
At best, complexity only buys time when trying to crack passwords.
For example, recently I was reading a book about an FBI agent which asserted that it took the government fbi (or nsa) supercomputers almost 6 months of continuously running, to crack a password which turned out to be "chewy12345". Even the FBI agent in charge knew very well that they got lucky.
(This was on page 148 in the paperback version of the book "American Kingpin" by Bilton).
I'm guessing this password cracking on the fbi/nsa supercomputers, was likely a sophisticated dictionary attack. A brute force attack of going through every possible 10 character password string without any obvious structure, would likely take considerably longer than six months.
jcroy
Senior HTF Member
- Joined
- Nov 28, 2011
- Messages
- 7,932
- Real Name
- jr
My guest wifi password is:
ywngtwp###
where ### is my house number. The phrase is "you will never guess the wifi password" - and my son just doesn't *get* that "password" is *one* word, not two. Every time he comes in with a new device he messes it up and I have to remind him password is *one* word.
Something like "you will never guess the password" might eventually become a part of generic password cracking programs, as a part of a list of thousands of common phrases to use as a starting point for a more sophsticated dictionary attack.
Before digital encryption became common, the equivalent of this algorithm was a spy using a particular book as the encryption key. For example, such as the encryption key being a string consisting of the first letter of each chapter in ascending (or descending) order.
Last edited:
jcroy
Senior HTF Member
- Joined
- Nov 28, 2011
- Messages
- 7,932
- Real Name
- jr
The more the merrier: The new NIST password guidelines suggest an eight-character minimum when the password is set by a human, and a six-character minimum when it’s set by an automated system or service. They also recommend encouraging users to create lengthy passwords with a maximum length of 64 characters or higher. All applications must permit any printable characters listed within the American Standard Code for Information Interchange, including spaces, and should even accept UNICODE characters (like emojis).
The 8 character minimum has been the standard for decades with the old now-deprecidated/obsolete DES encryption algorithm.

Data Encryption Standard - Wikipedia
DES had 56-bit keys, which seemed kinda odd on the surface. The only rationale I can think of for 8 character passwords using DES, is if the characters were 7-bit ascii characters. So 7 bits/characters * 8 characters = 56 bit keys.

ASCII - Wikipedia
The current american government grade encryption algorithm is AES with key sizes of 128 bits, 192 bits and 256 bits, which is used for encrypting classified information.
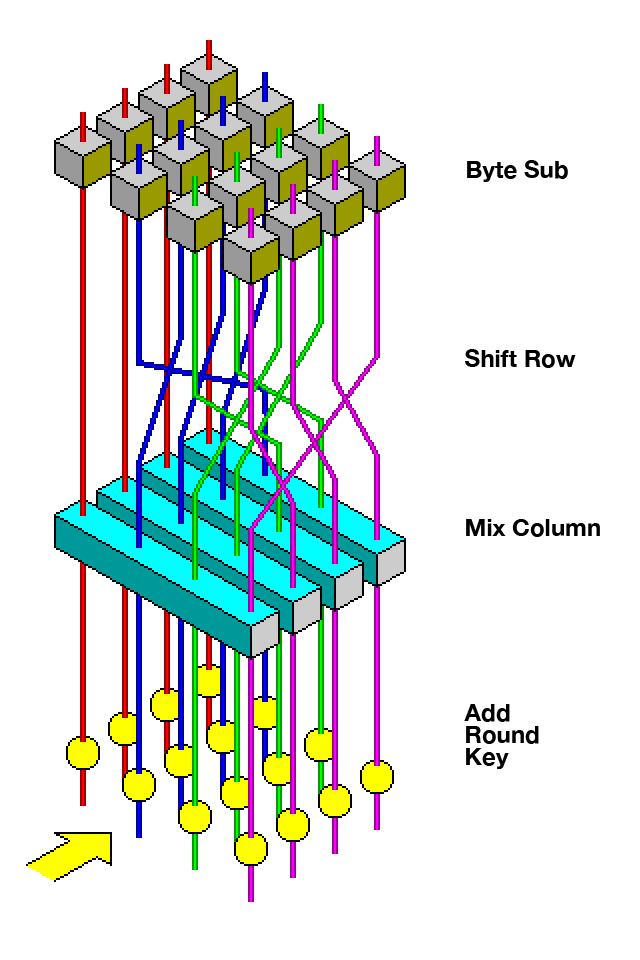
Advanced Encryption Standard - Wikipedia
Nowadays the minimum character set size would be likely 8 bits unicode. So if one wants to use all 128 bits of an AES key, the password should be 128/8 = 16 characters. Respectively 192 bits keys -> 24 characters, 256 bits keys -> 32 characters

List of Unicode characters - Wikipedia
Last edited:
Inconsiderate / entitled people get under my skin more and more especially this past year. People that drive like idiots and act like it is complete ok for them to do so. People that can not keep there hands off there phone and are constantly finding excuses to text someone every single time the come to a stop and sometimes when they are driving. Some have the worst habits and the moment you call them out on anything they go from 0 - angry just like that. Is it any wonder our society is going down the toilet? Computer asking if you want to store a password! While it would be convenient then it because easier for a hacker if your computer becomes compromised. And the ever evolving demands of what a password should be making it harder and harder to remember especially if use different passwords for many sites. Not to mention people who refuse to wear masks. People who claim to be tolerant but are actually on the other end of the scale. And being stuck at home with nothing to do!
Jeffrey D
Senior HTF Member
- Joined
- Oct 15, 2018
- Messages
- 5,221
- Real Name
- Jeffrey D Hanawalt
Yes drivers who don’t possess manners are my pet peeve too. I had an all-timer a couple of weeks ago- a guy was going to pass me at a red light from the left to enter a Wal Mart parking lot, and there was plenty of room behind me and a right turn lane that he could have used. I just shook my head- what else is there to do? Moron drivers are part of life, and sometimes it’s hard to not give them the 1 finger salute or yell at them.Inconsiderate / entitled people get under my skin more and more especially this past year. People that drive like idiots and act like it is complete ok for them to do so. People that can not keep there hands off there phone and are constantly finding excuses to text someone every single time the come to a stop and sometimes when they are driving. Some have the worst habits and the moment you call them out on anything they go from 0 - angry just like that. Is it any wonder our society is going down the toilet? Computer asking if you want to store a password! While it would be convenient then it because easier for a hacker if your computer becomes compromised. And the ever evolving demands of what a password should be making it harder and harder to remember especially if use different passwords for many sites. Not to mention people who refuse to wear masks. People who claim to be tolerant but are actually on the other end of the scale. And being stuck at home with nothing to do!
There are also drivers that will pass you on the right when there is no lane before the signal because they want to get around everyone. And then there are those who insist on being up on your bumper even when you keep pulling forward they refuse to give you any space. So then if they get rear ended there is a better chance there vehicle gets pushed into yours.Yes drivers who don’t possess manners are my pet peeve too. I had an all-timer a couple of weeks ago- a guy was going to pass me at a red light from the left to enter a Wal Mart parking lot, and there was plenty of room behind me and a right turn lane that he could have used. I just shook my head- what else is there to do? Moron drivers are part of life, and sometimes it’s hard to not give them the 1 finger salute or yell at them.
jcroy
Senior HTF Member
- Joined
- Nov 28, 2011
- Messages
- 7,932
- Real Name
- jr
For the longest time, I was one of those lousy/inconsiderate drivers myself.
Gradually over the years I was taking more cabs (or occasionally public transportation) into the middle of town for work, instead of driving.
(Without getting heavily into politics).
Nowadays I understand why some really rich folks don't even bother getting a driver's license (such as possibly the now ex-pres). All the traffic liability is with the hired cab (or limo) service. Not easy to tie any traffic liability to a person who doesn't have a driver's license, and who doesn't speak with the driver.
Gradually over the years I was taking more cabs (or occasionally public transportation) into the middle of town for work, instead of driving.
(Without getting heavily into politics).
Nowadays I understand why some really rich folks don't even bother getting a driver's license (such as possibly the now ex-pres). All the traffic liability is with the hired cab (or limo) service. Not easy to tie any traffic liability to a person who doesn't have a driver's license, and who doesn't speak with the driver.
jcroy
Senior HTF Member
- Joined
- Nov 28, 2011
- Messages
- 7,932
- Real Name
- jr
The more the merrier: The new NIST password guidelines suggest an eight-character minimum when the password is set by a human, and a six-character minimum when it’s set by an automated system or service.
Thinking about this 6 character minimum password, this might make sense if such passwords are generated randomly. For such randomly generated passwords, a dictionary attack would be not be very effective at all. So this would mean going through every possible password sequentially by brute force.
A randomly generated password at minimum would likely consist of printable ascii characters on a typical american qwerty keyboard. There are 95 printable ascii characters, while the remaining 33 characters are non-printable and/or control type characters (such as backspace, tab, return, carriage return, etc ...).
For simplicity, there are around 100 ascii characters which could be used for generating such random passwords. (ie. Take your five favorite non-printable/control type characters such as backspace, tab, etc ... in addition to the 95 printable ascii characters).
So for a 6 character password, there are 100^6 = 10^12 = one trillion possible password strings to go through !!!
For context, try running a computer program which just counts from 1 to a million and time how long it takes to finish. Multiply that time by another 1 million factor, which will give you a good idea how long it would take to do brute force cracking of 6 character passwords with are randomly generated with no obvious human linguistic structure to the passwords.
Re: the password issue - Once again, everyone should be using a good password manager and letting it set a random password utilizing all of the maximum allowed rules on any given website. If a website allows upper case, lower case, numbers, and symbols with a maximum length of 64 characters, that should be how you set your password for maximum protection.
Chip_HT
Screenwriter
- Joined
- Jun 28, 2004
- Messages
- 1,096
- Real Name
- Chip
Pretty sure we've been over this one before, but still....when Amazon has some issue with shipping an order and just opts to cancel it and refund instead of just shipping it out again.
And it still takes 3-5 days to process the refund. How does it take longer to refund than it would to ship?
And it still takes 3-5 days to process the refund. How does it take longer to refund than it would to ship?
Users who are viewing this thread
Total: 1 (members: 0, guests: 1)
Sign up for our newsletter
and receive essential news, curated deals, and much more
Similar Threads
Members online
- darkrock17
- Jonathan
- Yeoman007
- Worth
- dana martin
- battlebeast
- dstrong
- Walter Kittel
- LouA
- Joe Wong
- TPWard
- Flashgear
- Powell&Pressburger
- DVBRD
- Chelsearicky
- FrankXS
- borisfw
- Alan Tully
- xochipilli
- Dennis Gallagher
- Geercklay
- JimJasper
- pjones
- BobO'Link
- TonyD
- jkholm
- Gary OS
- Kevin Korom
- YANG
- Adam Lenhardt
- Josh Dial
- Stefan Andersson
- TJPC
- Osato
- ahollis
- rjd0309
- Konstantinos
- Brian Husar
- MaconBacon
- dpippel
- Ken H
Total: 1,043 (members: 48, guests: 995)
